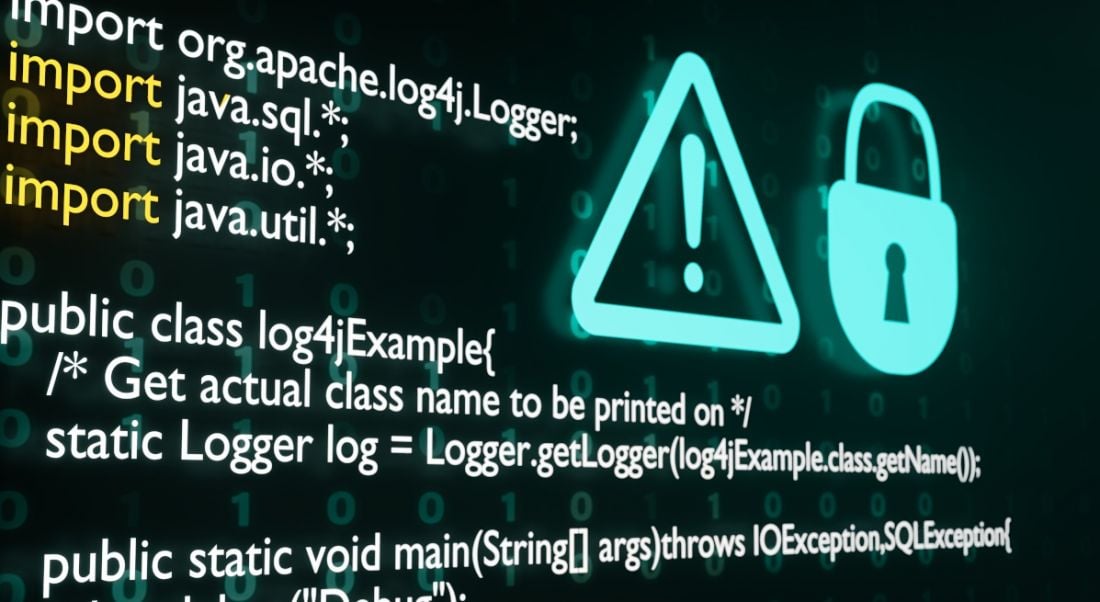
The aim of the course is to train teams about what the Log4j vulnerability is, what it impacts and what steps organisations can take.
Tech workforce development company Pluralsight has introduced a free course that deals with the Log4j vulnerability.
The course is being launched in response to the Log4Shell cybersecurity flaw that has recently been making headlines. It offers an overview of what the vulnerability is, what it does and does not impact, and some steps organisations can take to test the vulnerability.
Participants can take the course for free on Pluralsight’s online learning platform.
Log4j is a Java-based logging utility that is used by many companies for their web infrastructure, including Microsoft, Apple, Amazon, Cisco, Tesla, Twitter and Baidu. The recently discovered Log4j flaw could be exploited by hackers to gain access to computer systems.
Last week, Ireland’s National Cyber Security Centre (NCSC) issued a warning to all companies that use web servers to respond to the threat, dubbed Log4Shell. The NCSC said that Apache, which maintains Log4j, had published an update to patch the flaw.
The US government has also urged caution in the face of the potential security threat.
Brandon DeVault, senior security author at Pluralsight, said the flaw received a CVE score of 10, which “is rarely seen”. CVE, or common vulnerabilities and exposures, is an assessment of publicly disclosed computer security flaws, with 10 being the score for the most severe vulnerabilities.
‘This is the highest criticality score a vulnerability can get,” DeVault added. “The vulnerability allows an attacker to replace fields, or things being logged with malicious code. In simple terms, this has the potential to give an adversary full control over the vulnerable application. Depending on where that application sits, this can give full access to a network.
“Simply patching Log4j is more complicated than doing a single sweep through your network and applying a patch. Since Log4j is used as an open-source logging plug-in for thousands if not millions of applications, it will take a while for organisations to even figure out what applications within their network are using it.”
Pluralsight’s course, Log4j vulnerability: What You Should Know, includes a Q&A session discussing the Log4j flaw. The aim is to inform teams about why this is such a critical and widespread vulnerability and how companies can identify if they’ve been affected.
Don’t miss out on the knowledge you need to succeed. Sign up for the Daily Brief, Silicon Republic’s digest of need-to-know sci-tech news.